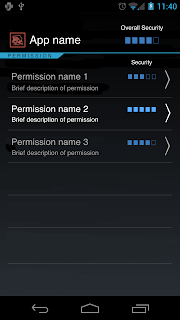
Hello again. Below are two of my rough designs for a user interface. The idea behind them is that when users attempt to install a new app, instead of allowing the usual screen display the permissions the app requests, one of them will come up. The screen will display a security score for the app overall and then a score of each individual permission requested. Yet, these designs have multiple flaws, such as the scoring system.
As these are rough drafts, multiple revisions will follow. For now I will focus more on the second design, as it is the simplest. What do you think?
- Eunice.
Sunday, September 30, 2012
September 28 Meeting
Hello,
In this meeting, as Danny pointed out, we went over our ideas for a user interface design. Dr. Zheng suggested that we combine a few aspects of our UIs and add a few more things; however, since Danny and I are working independently on this portion of the research, the designs must be created independently. Once we have settled on one or two creations, the next step is to proceed with the actual implementation. Nonetheless, next week the team will meet again to discuss the UI revisions.
In the next post I will provide examples of my design and discuss their features.
- Eunice.
In this meeting, as Danny pointed out, we went over our ideas for a user interface design. Dr. Zheng suggested that we combine a few aspects of our UIs and add a few more things; however, since Danny and I are working independently on this portion of the research, the designs must be created independently. Once we have settled on one or two creations, the next step is to proceed with the actual implementation. Nonetheless, next week the team will meet again to discuss the UI revisions.
In the next post I will provide examples of my design and discuss their features.
- Eunice.
Friday, September 28, 2012
The past 2 weeks
After 2 weeks of steady progress leading up to this mornings meeting, some good ideas have been developed and refined. During today's meeting both mine and Eunice's visuals representation for risk scores that we give to apps were presented for the first time. My ideas need some refining before becoming a final draft, but keeping the representations simple and familiar to the user, I believe will yield the best results. Below is a preliminary idea that I developed for both presenting the risk score of an app as well as for bring the users attention to the permissions that are of higher risk. Over the next week I hope to come up with a near final product. Until then!
-Danny
-Danny
Sunday, September 16, 2012
September 14 Meeting
In this meeting, Yang Wang presented to us how some Android permissions work. Additionally, he taught us how the risk of a permission is evaluated (summary: it involves a summation of likelihood of adverse event * impact of such event). For the risk analysis 169 standard permissions will be considered; thus, any user-defined, manufacturer-defined, or obscure permissions cannot be rated. As to how Android permissions are deemed normal or dangerous, it remains unknown to us.
During the rest of the meeting we talked about the particulars of how to proceed with our work: we are downloading the Android 4.0 source code, we will need to recompile the OS, etc.
By next week, Danny and I will post possible user interfaces.
- Eunice.
Wednesday, September 12, 2012
Introduction to the New Cast
Hello. After some delay, we get to introduce the new cast of the NMT CREU. This year, two Computer Science students will develop new Android app installation interface that indicates to the user the risk of installing a program (or app) based on the permissions it requires. By doing such, they will determine if their method of presenting the information is effective in teaching the general audience about Android permissions. This semester, their work will focus on designing and implementing the installation interface.
And now, the actors:
Daniel Fahey
And now, the actors:
Daniel Fahey
Daniel currently is a junior, majoring in Computer Science at New Mexico Tech. Grew up in Albuquerque, New Mexico. He enjoys developing personal android apps for fun and for use in productivity for day to day tasks.Eunice Perez
Eunice is a junior working toward dual major in Mathematics and Computer Science at New Mexico Tech. Some of her academic interests include statistics, stochastic processes, and algorithms. On her free time she enjoys learning about the causes and effects of human reasoning and behavior.- Eunice.
Subscribe to:
Posts (Atom)